(Updated at 2020-09-19 19:13) – Good news, everyone. bxsmail.com is not responding anymore. Could one hope Telia booted mr Spammer off the net? Probably just a minor setback until he finds a news place to send his crap from. Pyrobee.com is, alas, still up and running. Why, oh why…?
How the journey begun….
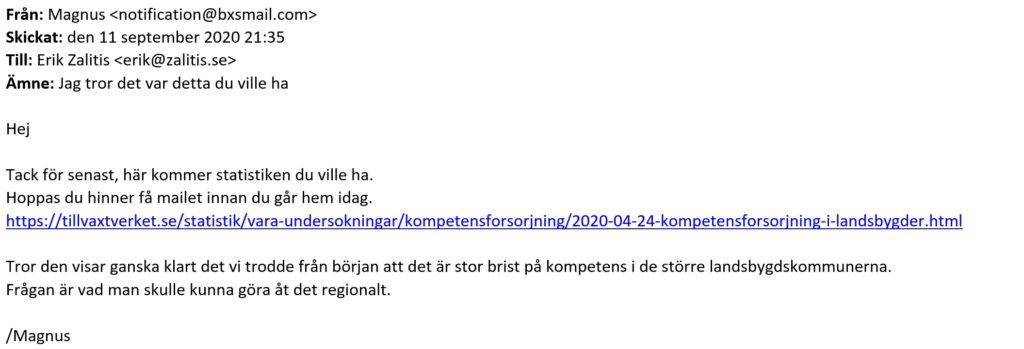
On Friday the 11th of September I found an email in my junk mail folder. That in itself is nothing special, but this particular spam stood out. It was in Swedish, without the usual auto-translated mess that those are wellknown for. It simply said (translated from Swedish):
Hi
Thanks for the last time, here are the statistics you wanted. I hope you’ll receive this mail before going home for the day.
<Link to what looks like tillvaxtverket.se, but really sends you to a malicious site>[I] believe it rather clearly shows what we though from the start and that is that there is a large lack of available talent in the rural communes. The quiestion is what could be done about it on a regional level.
The Swedish original:
From: Magnus notification@bxsmail.com
Sent: den 11 september 2020 21:35
To: Erik Zalitis erik@zalitis.se
Subject: Jag tror det var detta du ville haHej
Hoppas du hinner få mailet innan du går hem idag.
hxxps://tillvaxtverket.se/statistik/vara-undersokningar/kompetensforsorjning/2020-04-24-kompetensforsorjning-i-landsbygder.html
Tror den visar ganska klart det vi trodde från början att det är stor brist på kompetens i de större landsbygdskommunerna.
Frågan är vad man skulle kunna göra åt det regionalt.
/Magnus
I racked my brains trying to remember ever having spoke to someone on Tillväxtverket about something that would warrant this response and came up empty handed. I quickly Googled and what I found made me suspect it was some kind of fraud or spam. I posted my preliminary findings on “Säkerhetsbubblan”, a Facebook group dedicated to IT-security discussions.
At this time I was quite curious about what was going on and started tracing the sending system down. The mailheaders were clear on the matter.
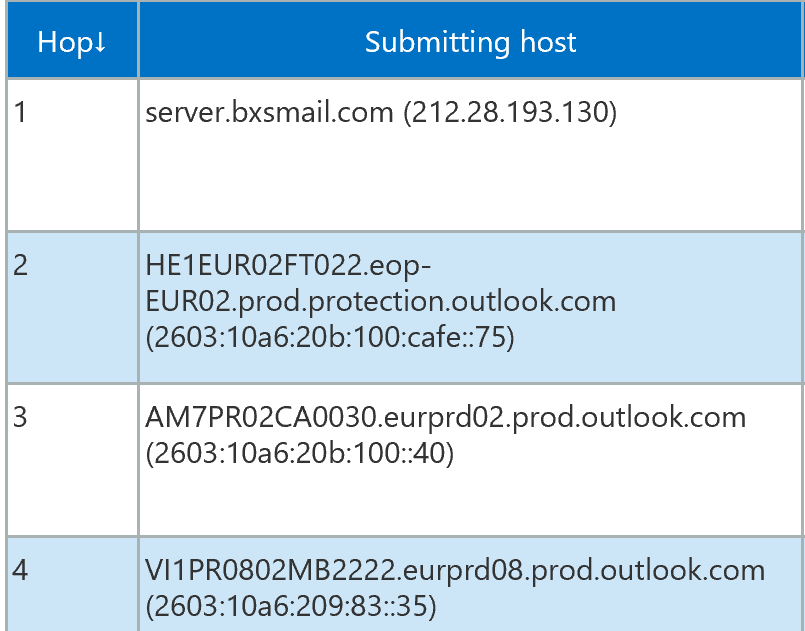
The IP was recognized almost immediately by me, as I used to work at Swedish telecom provider Telia back in the day, and sure enough, it was them.
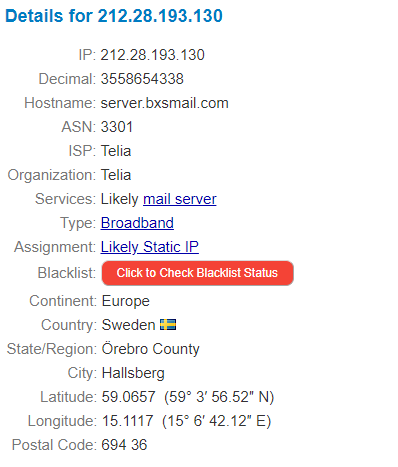
The post code is easy to put on a map:
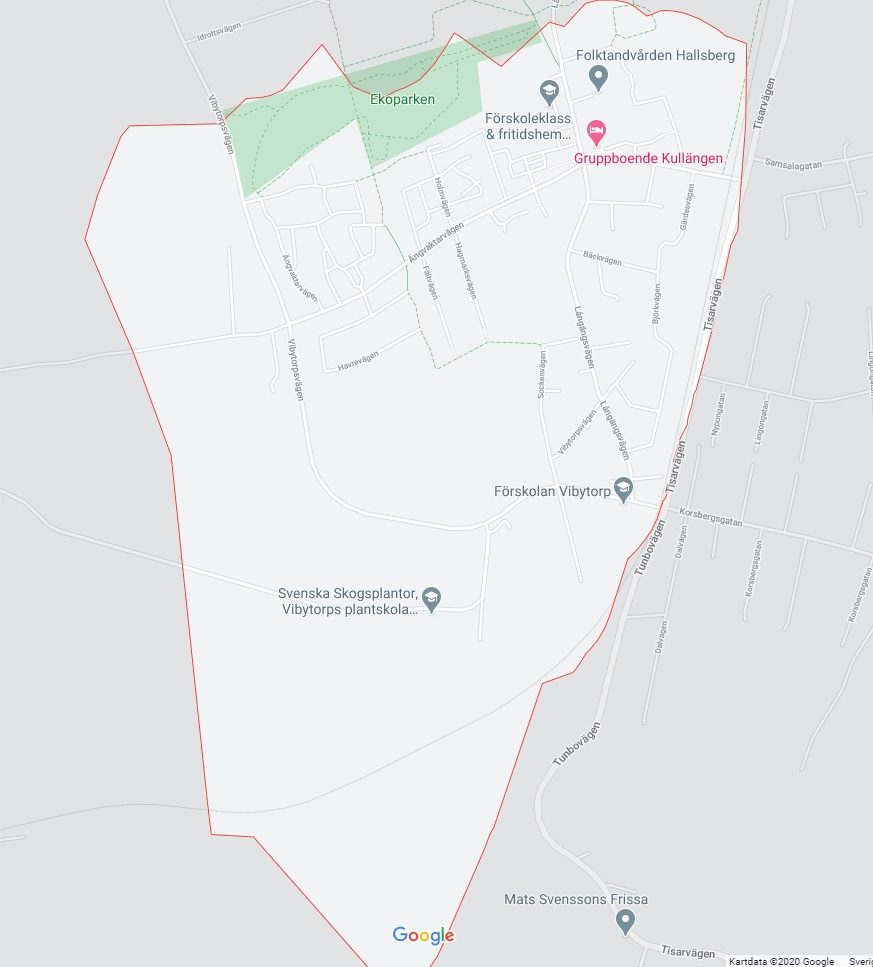
A typcial war zone in Sweden. A few day care centers for children and small suburban housing. This is where the hacker roams freely…. or maybe not. Seriously though, it’s probably located on someones home network, directly connected to a consumer Internet broadband connection operated by Telia.
One click on this link and you’re toast…
Let’s take a look on the seemingly innocent email (you should know better now, though):
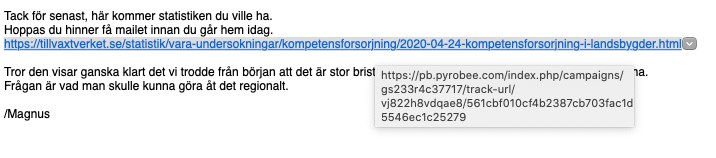
Hovering over the link in the email, shows you where it really goes. The link leading to the Tillväxtverket-site uses an old trick, where the displayed link does not correspond to the one you’re actually are clicking on (Se picture above!).
Weirdly named proxy “Burp suite”, shows exactly what happens over the wire when you click the evil link like there was no tomorrow.
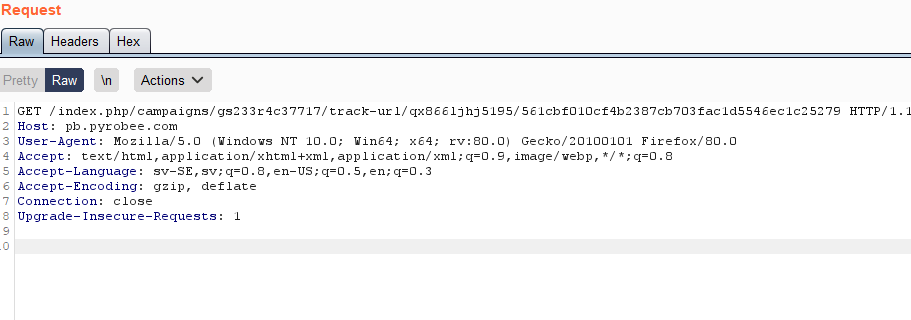
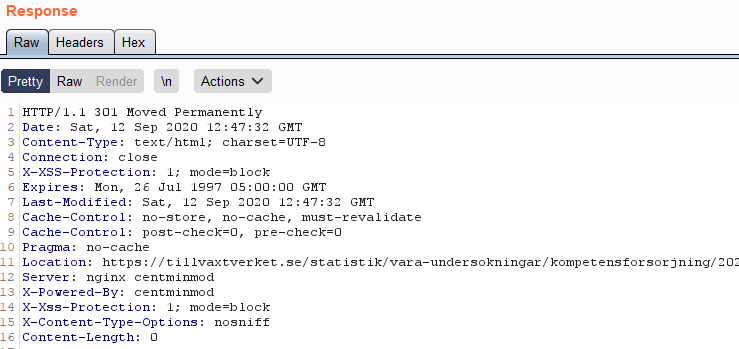
This fake link instead leads to a server for the domain pyrobee.com which is located in Germany. The reply-to address in the mail also points to info@pyrobee.com. The ip-information for this site is as follows.
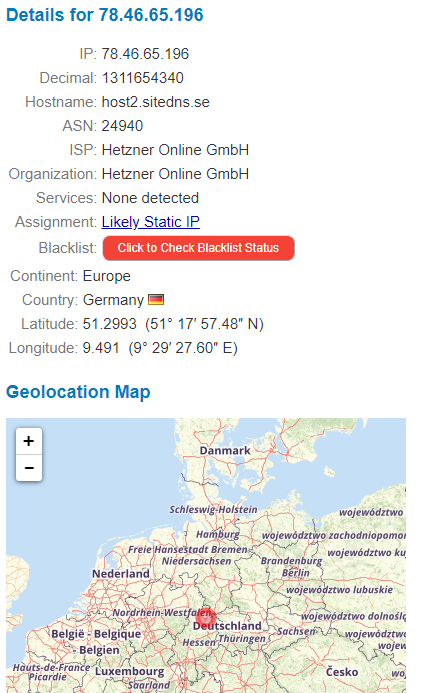
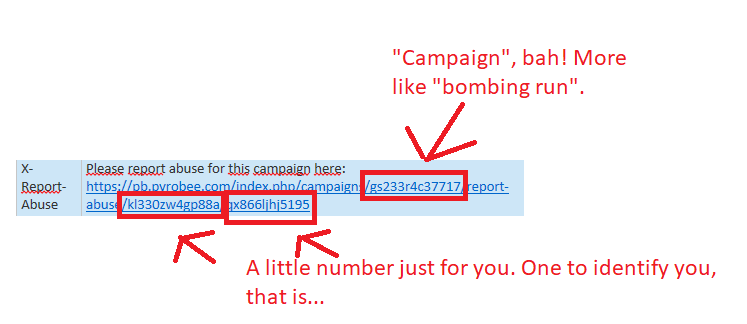
If you somehow doubt they are malicious, note the abuse-link provided in the mail:
OH!! They have a Facebook presence too… How “I’m just a serious business owner” of you.
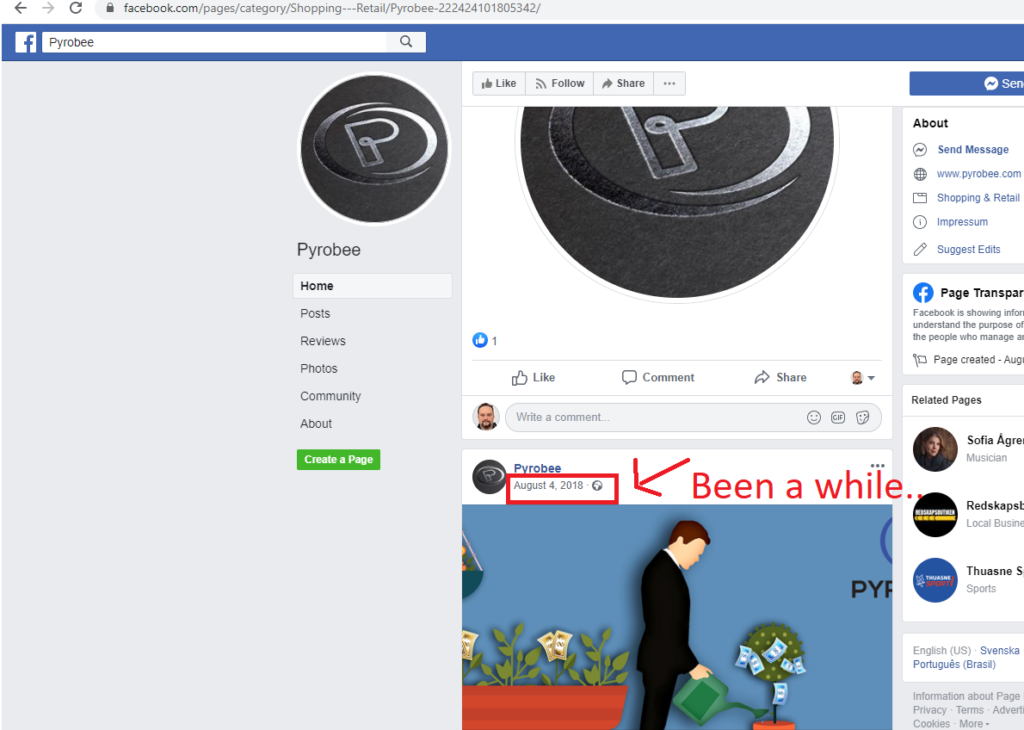
And for my final trick, I going to pull a rabbit out of my hat. Or rather, disclose the identity of the spammer. He seriously has his REAL name on the FaceBook-group above. A fast check shows that he lives in the exact same area and in the same Zipcode as the bxsmail.com-server is located.
This links him to the Pyrobee.com-server AND the bxsmail.com-server. So it’s a wrap then? We’ll see.
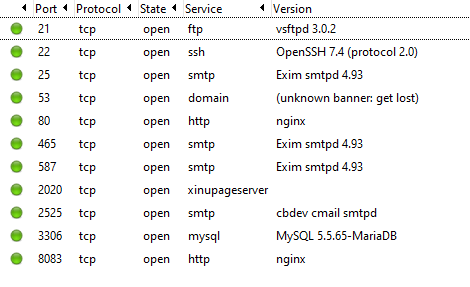
What about them servers?
So, back to the server in Sweden, server.bxsmail.com. What is it running? Quite a lot actually.


We can go no further as this would constitute an intrusion, and I’m strictly a white hat.
Analysis
Given what we know:
- The link in the email takes the user clicking on it on a detour to pyrobee.com, a server in Germany, and then automatically bouces the unwary user to Tillväxtverket. This way, it will look legit. This link has, what looks to be a identifier, that is most likely connected to the email-adress the mail was sent to. Thus the Pyrobee.com-server will know who clicked on the link.
- Most likely this gives the hacker a list of people that clicked on the link and who can now be further investigated and targetted for phishing attacks in the future. Caveat emptor: don’t click the link! (Unless you’re like me, curious and want to see what happens..)
- It’s impossible to say if this attack was aiming to target Tillväxtverket in any way or capacity, or if they were selected to give the attack itself a semblance of credibility.
- The server sending the email is barely configured at all and only the services needed to send the emails seem have anything more than just minimal “dial tone”-setup.
- It’s likely not to be secured in any meaningful matter. I cannot, as I stated, investigate this any further
- The server in Germany uses a template that teases with stuff like podcasts and a blog, but in reality does not exist. It’s kinda a good thing to remove services featured on the template by default, if you don’t intend to offer them. Looks more serious like that.
- Real advertising campaigns often work exactly like this, but they generally don’t use badly built servers running on someones home broadband connection and then redirect you to another, barely setup server in Germany. Also, they DO NOT SEND spam that tries to fool you that the message is an answer to a previous discussion with the sender that obviously did not happen.
Time line
2020-08-07 – The domain bxsmail.com was registered. It’s probably around this time the mails started appearing.
2020-09-11 – I noticed the mail, that was sent to my private email address, in my junk folder and started to investigate the matter. Had to stop due to needing to sleep.
2020-09-11 – Asked Telia to shut the server in Sweden (bxsmail) down.
2020-09-12 – Sporadic work in spare time during a trip to another city in Sweden.
2020-09-12 16:12 – completed the report after some questions were asked and then added new stuff I found.
2020-09-12 16:23 – reported Pyrobee.com to their upstream provider’s abuse department.
2020-09-12 17:xx – reported spam to spamcop.
2020-09-13 19:xx – They have now created more domains with servers: ettmoln.com and merkurex.com. Probably not a complete list, but I will update as soon as I learn more… Their weak point is pyrobee.com. Take that down and they will have nothing going on.
2020-09-12 22:31 – The identity of the owner of all the servers has been found. He wrote it on Pyrobee’s FaceBook-page. The name is Magnus, but I will not write his whole name here as to stay within the Swedish law. He lives exactly in the same postal code (zip code) area where the bxsmail.com server is located. I have a hard time believing this… Really takes the cake.
2020-09-14 – Right, I was told by the German abuse-department that they will not process the report unless they can tell the owner about it. That will effectivly send this link to the guy behind all this. Who said life should not be interesting?
Evidence and other material
The spam mail, complete with all headers:
https://erik.zalitis.se/files/spam.txt
Thanks
Malin Ekström for spotting a thing I missed.
The rest of the “Säkerhetsbubblan“-Facebook group for aiding me in my research… You guys and gals rock.
If you have a look in the RIPEdb it looks like there are three /24 prefixes allocated by Telia to “MG” and Neonex dating back to 2011:
https://apps.db.ripe.net/db-web-ui/query?bflag=false&dflag=false&inverse=org&rflag=true&searchtext=ORG-NA407-RIPE&source=RIPE
Looking a bit at the reverse PTR pointers in those subnets there seem to be connections(customer or otherwise) to the firm FL-net and “ML” with a long history of being active in the email marketing business, obligatory Flashback thread:
https://www.flashback.org/t1119882
My guess is that this is one of them testing out one of many harvested or bought email lists for further marketing use…
As an aside, it seems that this “MG” is also active exploiting fears around the current pandemic peddling masks through his Estonian company Northlogix OÜ over at gnix (dot) se.
Hey, thanks.
That’s great info. It sheds some light on this from bigger perspective…
Regards/Erik