I was working from home one Friday as Dnov sent me an email asking for my participation in the FOI 20/20 CTF. I thought about it, and decided to join him and his crack (haha!) squad of elite haxx0rs. A “capture the flag” or CTF is simply a hacking competition, where you work as a team to solve tasks that require you to “hack” something. It does not necessary mean rooting a system, but you have to subvert a service, program or system in order to prove your skills in breaking its security.
FOI – Totalförsvarets forskningsinstitut
FOI is a Swedish governmental organisation tasked with aiding the Swedish armed defence with technology research and support things like disarmamernt and international security. In a typical Swedish manner, doing a lot of things that looks like they’re contradictionary. 🙂
On the 26th of September the 20/20 CTF started with a bang as the virtual doors flung open at 2 pm and we worked until 10 pm that same evening.
Meet 0xDEADBEEF
In the Atrocity archives, supernatural hacker/sysadmin/government agent Bob Howard destroys the content of a hard drive by writing the hexdecimal string DEADBEEF over and over again on all the tracks. This is as far as I know an old hacker joke and it fits. 0xDEADBEEF is also the name of our team. We’re at this moment five guys employed in the IT-security field. So let’s talk about us.

dnov
The principal leader of the team. He’s like that white haired old man who likes a good plan coming together in the A-team TV-series. With a broad knowledge in infosecurity, it-security and working with our Swedish defense effort, he is really the right man for the job.
CrashOverride
Ok, so we’re doing A-team references here? This is clearly Mr T. The heavy hitter, who managed to come up with solutions to many different tasks and worked all over the board mostly with cryptograhy and reversing. He has an academic background “in something cyber”. That’s his story, and I’m sticking with it. So there…
StripeCAT
Enough references to the old TV-series, as I really don’t remember it all that well. But StripeCAT is my nome de guerre and I’m a good supporting role, with plenty of experience with web hacking and network (in)security. Know my way around Kali Linux and Burp suite and Metasploit.
FX
Working in the same company as dnov and specializing in webhacking and security analysis.
Zaffner
General profile with experience in a number of different areas.
A journal of sorts… Because, why not?
Saturday, the 26 th of September
10:00 woke up late and spoke to my mother over the phone. Got on an uber to a music store in Järfälla to get my new mixing console. An errant soldering job had swiftly killed the one I had.
12:00 connected the new mixing console and patched the compressor into it. This made it possible to get sound to my rig. A good thing when you’re in a teleconference. Due to Corona, I decided not to go to the location where the others were gathering.

Made contact with the team on Slack. CrashOverride offered to come and get me into the building, until I pointed out I’m working from my home.
12:30 updated Kali Linux on my main PC as a virtual machine. Also had a real laptop with Kali on standby. “All events random favor the prepared” and all that.
13:00 ordered some food and made sure everything worked. At this time everyone in the team had arrived, with FX being the last to enter the room.
14:00 dnov was frantically smashing the “F5”-key to reload the CTF website, waiting for it to start. And sure enough, the challenges appeared on time.
We all started working. Zaffner took the first flag. Just a few seconds before I did. This is not a good thing, as it meant he missed that I was working on it. But dnov soon started coordinating the challenges so we would not work on the same ones unless cooperating. Doing so would otherwise make us lose valuable time.
The first tasks went down easy.
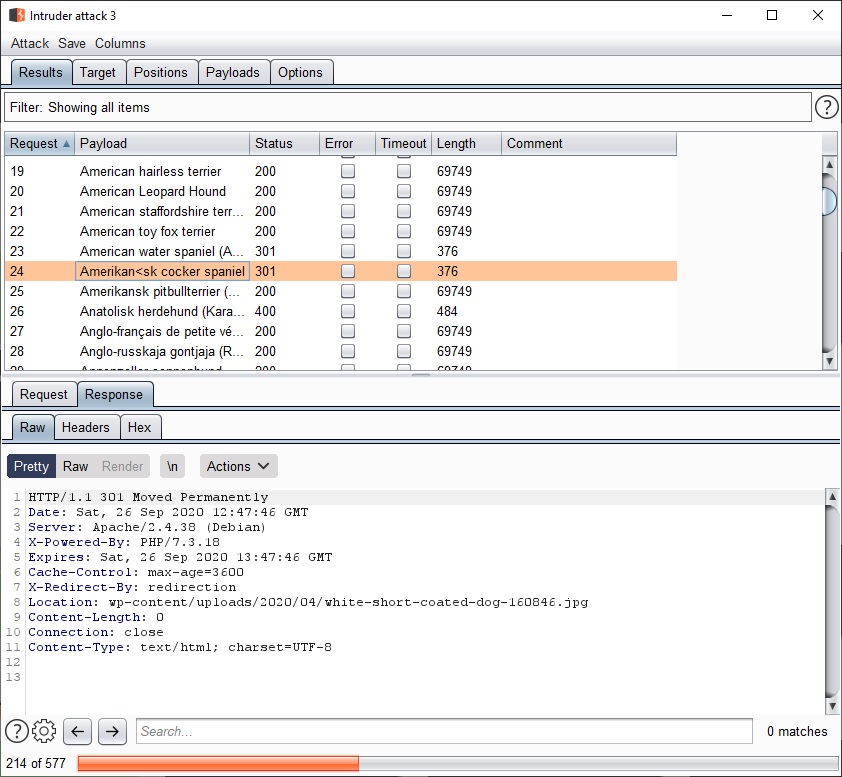
I fed a total list of all existing breeds of dogs into Burp suite and solved a very weird flag involving trying to figure out how to get a web app to give out information to some kind of dog collar that a normal user should not be able to get. It worked and I got a good laugh out of it.
The others worked through cryptography and reversing. One task spewed out simple aritmetic questions that had to be solved with in a few seconds. CrashOverride and Dnov quickly wrote a script to do so and the flag was caught.
FX and Zaffner looked into the arguably convoluted mess of a Javascript that held the secret to one of the flags.
I wrote a script to recursivly open encrypted ziparchives, but CrashOverride mistakenly solved it before I was done. Having lost two flags because of the others failed to note that I was on them made me a bit irritated, so I told them in no unclear terms to start keeping track on who is doing what. No more incidents after that, but my outburst probably rendered this choice of emoji representing me on Twitter from dnov:
… I find that highly amusing… 🙂
The afternoon went on and we steadily captured the flags. At one point we were ranked as number nine among the 152 competing teams and this energized us even further.

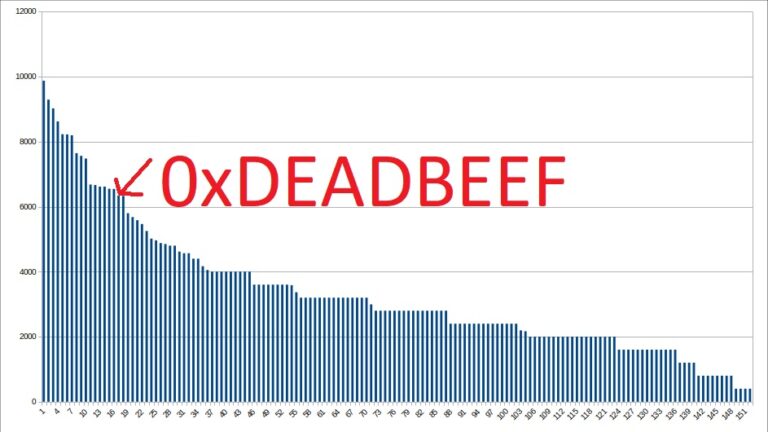
The remaining tasks were harder and it was pretty clear that the tasks on the right side of the list were the really hard ones. Each flag gives the team and the member points. The points decrease over time as others solve them as well. So looking on tasks that still have the full score you will see that no one else have been able to solve them either…
In the evening we ordered pizza and the team took a short break.
9 pm The night was looming and we were frantically trying to solve the last challenges. The final minutes had me and CrashOverride fighting with a very obfuscated javascript mess to find a flag.
10 pm All is over and the final score is in. We did quite well, but no prizes coming our way. 17th place, that rocks!
The aftermath
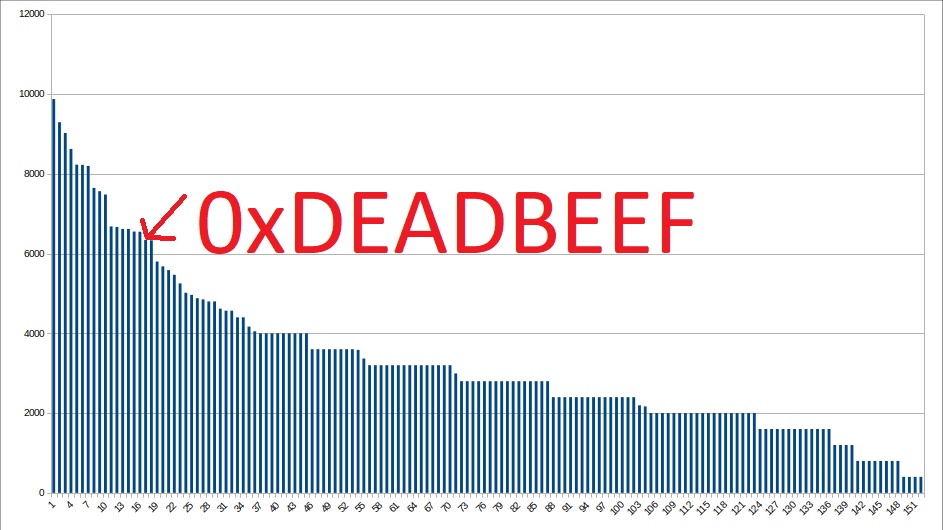
So… Did we do it well? Heck, yeah! But we also had fun and learnt a lot along the way. Much obliged.
The good
- A brand new team that had no problems getting into high gear.
- We hit the ground running.
- No real technical problems on our side. Except maybe with Zoom.
The bad
- Took a while before we started helping each other on a regular basis. At first everyone was focused on their tasks.
The ugly
- The test environment provided by FOI was a bit flaky at times.
The links
CrashOverride’s own write-up (In Swedish):
https://github.com/dansarie/FOI2020CTF/blob/master/README.md